- January 9, 2025

Web application security testing is the practice of safeguarding websites, their applications, and APIs from malicious attacks. It is a comprehensive discipline that focuses on the smooth functioning of web applications. It also plays a major role in protecting businesses from data theft, cyber vandalism, and unethical competition.
The APIs and web applications are constantly exposed to attacks from various locations and at different levels of scale and complexity. Therefore, web application security testing is mandatory, and it encompasses a variety of strategies to cover the major parts of the software supply chain.
Discover everything you need to know about API security testing, including its purpose, various types of testing methods, and the most common risks to watch out for when securing your APIs.
Table of Contents
Why is Web Application Security Testing Important?
Web application security testing helps to identify security vulnerabilities in web applications and their configurations. Testing the security of a web application involves sending different types of input to provoke errors and enable the system to behave in unexpected ways. These are referred to as negative tests, and they help examine whether the system is doing something that it is not designed to do.
Web security testing focuses on more than just testing the security features of the website, such as its authentication and authorization, which might be implemented in the application. It is equally important to test that the other features are also implemented securely. The goal of web security testing is to ensure that the functions exposed in the website application are secure.
Features that Will be Reviewed During Web Application Security Testing
There is indeed a non-exhaustive list of features that should be reviewed during web application security testing. Any inappropriate implementation of these features might result in vulnerabilities and pose a serious risk for the organization. Some of these features include,
- Application and server configuration, where the potential defects are related to the cryptographic and encryption configurations.
- Input validation and error handling, which includes cross-site scripting, SQL injection, and other common injection vulnerabilities caused by poor handling of input and output data.
- Authorization, which ensures the application can protect against horizontal and vertical privilege escalations.
- Authentication and session management vulnerabilities can result in user impersonation. Therefore, credential protection and strength must also be considered.
- It is mandatory to ensure that business logic is properly implemented, as it is important to most of the applications that enhance business functionality.
Three Most Common Web Application Security Threats
Web application security testing is crucial to ensuring the safety and security of online systems and their users. Daily reports of breaches and ever-changing security threats show that security is indeed a top priority in every organization.
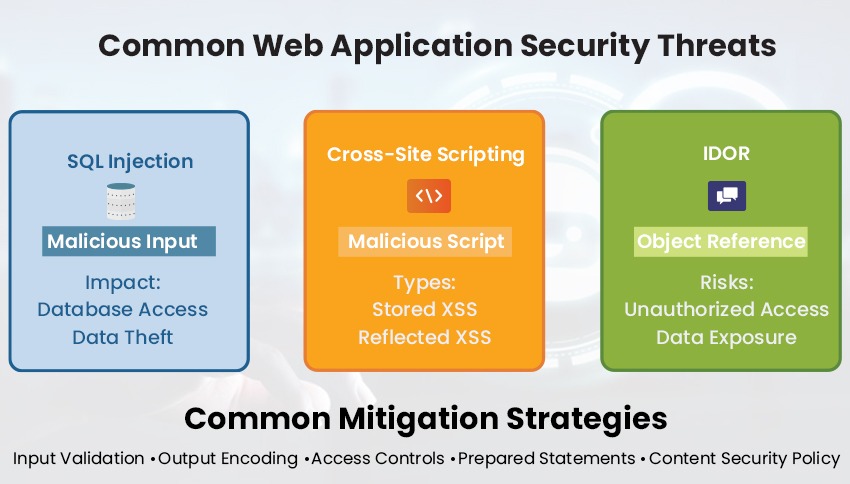
SQL Injection
A SQL injection attack occurs when the attacker injects the malicious code into the database of an application through user input fields. These types of attacks can achieve many different outcomes with major results like the attacker gaining access to the sensitive data in the database. This can be mitigated by validating user input, using output encoding, and using prepared statements.
Cross-Site Scripting (XSS)
Cross-site scripting attacks involve injecting malicious scripts and code into the website. The website will then execute the script, allowing the attacker to steal sensitive user data. There are two main types of XSS attacks: stored and reflected. XSS attacks can result in the theft of user session IDs, and this can be mitigated by validating user input, using output encoding techniques, implementing a content security policy, etc.
Insecure Direct Object References (IDOR)
IDOR occurs when the application exposes the direct object references, such as the database keys or the URLs, that allow the attackers to access the restricted data by manipulating the references. This attack can be mitigated by implementing proper access controls and session management. Validating the user input helps prevent the attackers from manipulating the direct object references. This can also be mitigated by avoiding the use of predictable references.
Want to learn about Top 10 Web Application Security Requirements for your business
Website Application Security Strategies
Web application security is a broad and constantly changing discipline. Its best practices change with the emergence of new attacks and vulnerabilities. The modern internet landscape is extremely active, requiring organizations of all types and sizes adopt certain web application security testing services to meet the specific needs of their business practices. Some common website application security strategies are as follows
Web Application Firewall
This helps to filter traffic that takes advantage of web application vulnerabilities. WAFs are extremely important as new vulnerabilities emerge too quickly and quietly for organizations to detect in time.
DDoS Mitigation
The DDoS mitigation services will sit between the server and the public internet by making use of specialized filtration and extremely high bandwidth capacity to prevent the surges of malicious traffic from stressing the server. This service is of extreme importance as most of the DDoS attacks deliver enough malicious traffic to overwhelm even the most resilient of servers.
API Gateways
These identify overlooked shadow APIs and block traffic suspected of targeting API vulnerabilities. They also help manage and monitor API traffic.
DNSSEC
This protocol guarantees that a web application’s DNS traffic is routed safely to reach the correct services and that an attacker route does not intercept users.
Management of Encryption Certificates
This web application security testing strategy uses third-party help to manage the key elements of the SSL/ TLS encryption process, which includes generating private keys, renewing certificates, and revoking them in the event of certain vulnerabilities.
Management of BOT
This security testing tool uses machine learning and other advanced detection methods to distinguish automated traffic from human users and prevent the former from accessing the web application.
Apart from these web application security testing measures, client-side security and attack surface management techniques help in checking third-party JavaScript dependencies and third-party code changes. They help the organization quickly identify potential risks, capture malicious activities, and mitigate them in a few clicks.
Web Application Security Testing – Best Practices
Web developers generally design and build website applications to prevent attackers from gaining access to private data and performing other malicious actions. They are also expected to adopt the following web application security testing best practices to mitigate risks effectively.
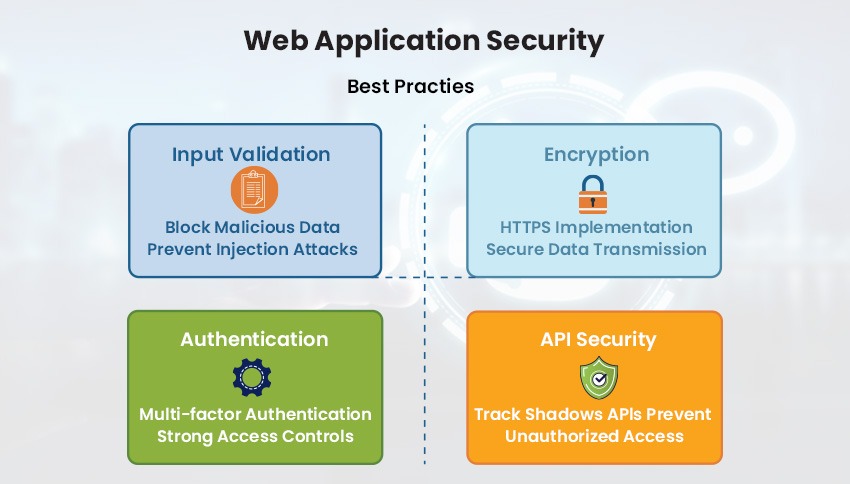
Input Validation
It is crucial to block improperly formatted data from passing through an applications workflow. This practice helps prevent malicious code from entering the application through injection attacks.
Using Up-To-Date Encryption
Encrypting user data and utilizing HTTPS to secure transmission of inbound and outbound traffic, helps prevent attackers from intercepting the data.
Strong Authentication and Authorization
Implementing and enforcing strong password controls, multi-factor authentication, access control mechanisms, hard keys, and other practices, makes it significantly harder for attackers to access user accounts fraudulently and navigate within the application.
Keeping Track of APIs
Some tools can identify overlooked shadow APIs, which might constitute an attack surface. Ensuring API security from the initial development phase is essential to prevent unauthorized access.
Different Types of Security Tests
Web application security focuses on building websites to function as expected, even when under attack. It involves the collection of security controls that are engineered into the web application to protect its assets from malicious agents. The process leverages secure development practices and implementing security measures throughout Software Development Life Cycle (SDLC). The different types of security tests employed to ensure that design-level flaws and bugs are addressed include,
Dynamic Application Security Tests (DAST)
This automated application security test is optimal for low-risk applications that need to comply with regulatory security assessments. For medium risk and critical applications undergoing minor changes, combining DAST with manual web security testing for common vulnerabilities is the optimal solution.
Static Application Security Tests (SAST)
This approach includes both manual and automated testing techniques. It is ideal for identifying bugs without the need to execute applications in a production environment. SAST enables developers to scan the source code and systematically find and eliminate vulnerabilities in the software.
Runtime Application Self-Protection
This evolving application security approach leverages various technological techniques to test an application. It enables real time monitoring of attacks and blocks them as they occur.
Penetration Testing
This manual application security test is ideal for critical applications, especially those undergoing major changes. It includes business logic and adversary-based tests to uncover even the most advanced attack scenarios.
How Does TestWheel help With Web Application Security Testing?
TestWheel offers a streamlined and efficient approach to web application security testing. By quickly identifying vulnerabilities in URLs and APIs, our platform ensures your web applications are protected against potential threats. Its intuitive and user-friendly interface makes the testing process simple for both beginners and experienced users alike. With TestWheel’ s comprehensive reports, you can easily assess the security posture of your application and take proactive steps to mitigate risks. Start testing now and protect your digital assets from vulnerabilities.



