- January 22, 2025

If your business primarily relies on the modern digital era, understanding web application security requirements is essential. Web application security refers to the series of processes, methods, and technologies for protecting web servers, web services, and web applications. It protects web servers and APIs from attacks by internet-based threats. Web application security is crucial in protecting data, customers, and organizations from data theft, harmful cybercrime and interruptions in the continuity of the business.
Table of Contents
Web Applications Security
According to estimates, about three-quarters of all cybercrimes will target web applications and their vulnerabilities. The web application security products and policies will protect the web application through certain measures such as multi-factor authentication, web-application firewalls, use and validation of cookies, and other measures to validate the user input to ensure that it doesn’t turn malicious before the input gets processed by the application.
Importance of Web Application Security
The world of modern times runs on apps, starting with online banking and remote work apps for personal entertainment, e-commerce, etc. Applications are indeed an important target for attackers, who will exploit vulnerabilities such as design flaws, weaknesses in APIs, problems in open-source code, access control, issues with third-party widgets, etc. This is where web application security requirements play a crucial role.
It serves as exceptional protection against attacks such as brute force attacks, credential stuffing attacks, SQL injection cross-site scripting attacks, and man-in-the-middle attacks. Cybercrimes can cost around $5.2 trillion in value by the year 2024, and the losses can reach about $6 trillion even before that. This is where security devices and technologies are crucial for limiting the costs. Apart from direct financial losses and consequences like data thefts and web application threats, it is possible for such attacks to destroy assets, business reputations, customer goodwill, etc. This, in fact, makes web application security a lot more imperative for organizations of different sizes.
How Does Web Application Security Requirements Work?
There are well-known approaches to web application security, all of which play a pivotal role in addressing different vulnerabilities. Web application firewalls are comprehensive tools that defend against various types of attack. They accomplish this by monitoring and filtering the traffic between the web applications and the end users. Web application security requirements are configured with policies to determine whether the website traffic is safe, and it is capable of blocking malicious traffic. It also works to prevent malicious traffic from reaching the web application and ensure that the app does not release any unauthorized data.
The web application security methods will primarily focus on access management and user authentication. They also encompass app vulnerability scanners, traffic visibility, cookie management, IP deny lists, and more. The advanced web application protocols will help organizations protect the apps and secure sensitive customer data by mitigating the application vulnerabilities with application layer encryptions and behavior analysis backed by threat intelligence and machine learning.
The Top Web Application Security Requirements for Businesses
Modern applications are sophisticated and complicated, with the injection of a host of third-party software, diverse hardware components, complex and distributed integrations, etc. But at the same time, these complications can also complicate the security posture. Every business requires web application security requirements to not just protect the business data but also to safeguard the reputation of the company. This is mandatory to keep up the trust of the customers and to adhere to the increasingly stringent regulatory requirements. Here are the top website security requirements that every business should possess.
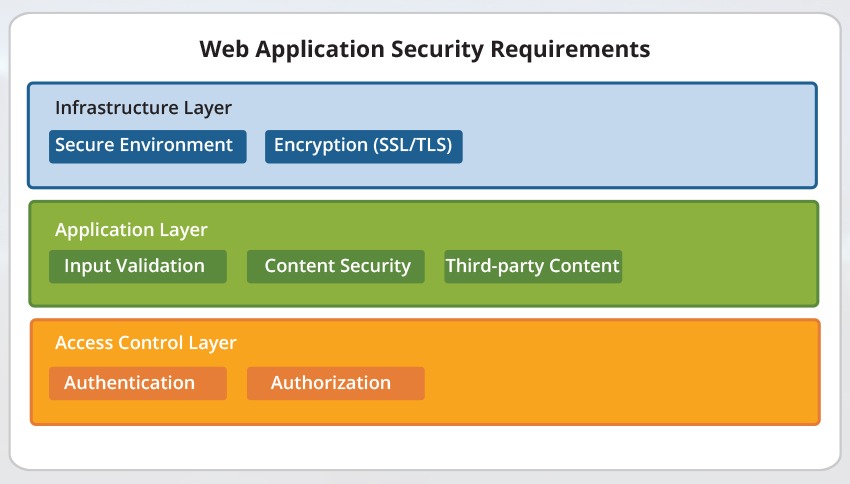
Maintaining a Secure Environment
Website application security should be hosted in the data center, on the business servers, or the Google infrastructure. Certain requirements and best practices help ensure secure operations. A web application will be secure if it operates in a secure environment. The security of all the application’s dependencies should be ensured. Some of these dependencies are the web application framework it is based on, the web server and the modules that are used by it, the underlying operating systems, the network components that lie between the user and the application, etc.
As a general rule, the software used around a business application should be up to date, and there shouldn’t be any known vulnerabilities that need to be patched. A robust vulnerability management process should be in place to ensure the prompt identification and remediation of the systems affected by the misconfigurations.
Input Validation
All the data and information that has been transmitted from the browser to the application can easily be manipulated by a malicious actor. In fact, the application should assume that the user input is always malicious. It is a misconception that the input that is received from the cookies, and hidden from the fields and the drop-down boxes cannot be manipulated by an attacker. It is possible to modify everything in the HTTP request, and thus stringent checks of all the input are mandated. It is also necessary to validate all the input that an application receives from any system that lies outside its trust boundary.
Managing Third-Party Content
Loading data from a third party could be dangerous for the website in certain circumstances, as the security issue at the third-party website might affect the downloaded application. To avoid this problem, the best practice is to avoid loading style sheets and scripts from any third party. Detecting embedded applets, frames, videos, and images from third-party sites could also be dangerous, as it might leak confidential information. In all instances where third-party libraries are not avoidable, these resources should be sourced locally, and care should be taken to download them from the latest versions. Communications should always be completed over the HTTPS connection.
Encryption
Attackers can easily listen in on packets transmitted between the user and the web application. To prevent sensitive data from being read by an attacker during transit, applications must have SSL only. To protect the application against such attacks, the webserver must be configured to support only TLS 1.1 or newer. It should accept only secure ciphers with strong key lengths.
Authentication
In most of the cases, the application or the data within the application should not be public. In order to control access, most of the applications will ask the users to log in. If the application is going to be used by more than a few people, it has to be integrated with the internal authentication mechanism. This ensures that the employees and others do not enter the account and give access to third parties. The application should offer season time-outs and the freedom to end the session manually for its users.
Authorization
Web application security requirements ensure that users cannot perform any unauthorized actions by accessing pages that are intended for a different purpose. If pages are shared across different roles and offer different functionality based on the user role, the application should take special care to allow appropriate actions for a specific role of the currently logged-in user.
Content Security
Content security is an in-depth mechanism that can be used to mitigate a broad range of content injection vulnerabilities, such as cross-site scripting (XSS). This goal is achieved through a declarative policy that enables the authors of web applications to inform the client about the sources from which the application expects to load the resources. Most modern browsers support some form of Content Security Policy (CSP).
Web Application Security Techniques and Tools
Static application security testing (SAST)
SAST solutions help analyze the source code to identify vulnerabilities and security risks. This scanning plays an integral role in multiple stages of software development, specifically when new code is committed to the codebase or during the building process.
Dynamic application security testing (DAST)
DAST is the process of testing both live and running applications to help uncover vulnerabilities. This testing can be performed automatically or manually, with the help of specialized tools. Automated DAST tools send numerous requests, including unexpected or malicious inputs, to the application to analyze the results for security weaknesses.
Penetration Testing
Penetration testing is a comprehensive security technique that combines dynamic scanning tools with human expertise to discover vulnerabilities in the security of the web application. As a pertinent web application security requirements, penetration testers will simulate real-world attacks by exploiting vulnerabilities, stealing data, getting unauthorized access, disrupting services etc.
Extended Detection and Response (XDR)
The web application security requirements will represent a new generation of the security solutions, providing security teams with an unified interface to respond to the threats across the entire IT environment.
Mitigating Security Risks in Modern Applications with TestWheel Comprehensive Approach
The increase in security challenges and the absence of appropriate practices significantly contribute to increasing security risks in today’s digital landscape. Modern applications face a multitude of threats, including vulnerabilities in open-source and third-party software, insufficient security awareness and training, improper access controls, and the lack of thorough risk assessments.
TestWheel addresses these challenges by collecting security data from all layers of the stack-networks, clouds, web applications, and endpoints. We leverage advanced analytics and automation to effectively meet the web application security needs of our clients, ensuring comprehensive protection and mitigating potential threats at every level.



